Hello Reader,
There is some interesting testing going on with shell item storage. The quirks of lnk files naming and storage by extension is surprising and needs more testing before its documented. Something that has been tested though is how many items a jumplist will store.
When Eric Zimmerman was first writing Jumplist Explorer we were discussing what the maximum amount of entries stored in a single jumplist could be. So we wrote some quick automation and found that a single jumplist will store approximately 2,000 items before it purges the oldest item. I suspect the hard limit is 2048 (power of 2) but in our testing it was when we reached 2,000 that older items began being deleted from the structure.
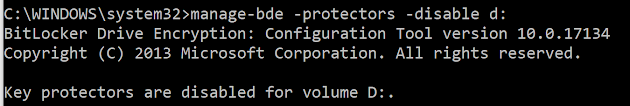
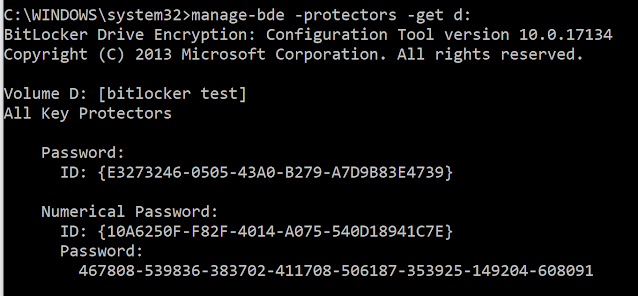
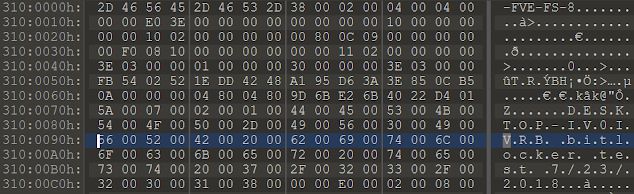
Now this does not mean the older entries are lost, the jumplist is a compound file system and the streams are just marked as deleted and available to be recovered until a new entry gets written over it. In fact Jumplist Explorer can recover deleted entries and mark them as such. Tomorrow I'll see if I can get screenshots of this happening and show the internal record numbers.
There is some interesting testing going on with shell item storage. The quirks of lnk files naming and storage by extension is surprising and needs more testing before its documented. Something that has been tested though is how many items a jumplist will store.
When Eric Zimmerman was first writing Jumplist Explorer we were discussing what the maximum amount of entries stored in a single jumplist could be. So we wrote some quick automation and found that a single jumplist will store approximately 2,000 items before it purges the oldest item. I suspect the hard limit is 2048 (power of 2) but in our testing it was when we reached 2,000 that older items began being deleted from the structure.
Now this does not mean the older entries are lost, the jumplist is a compound file system and the streams are just marked as deleted and available to be recovered until a new entry gets written over it. In fact Jumplist Explorer can recover deleted entries and mark them as such. Tomorrow I'll see if I can get screenshots of this happening and show the internal record numbers.