Hello Reader,
We had a forensic lunch today! It was just Matt and I as all of our scheduled guests had to reschedule but we made the most of our time. Thanks for those of you who tuned in live and expect Forensic Lunch to return in December on:
December 7th, 2018 at Noon CST
December 14th, 2018 at Noon CST
Matt and I talked about:
We had a forensic lunch today! It was just Matt and I as all of our scheduled guests had to reschedule but we made the most of our time. Thanks for those of you who tuned in live and expect Forensic Lunch to return in December on:
December 7th, 2018 at Noon CST
December 14th, 2018 at Noon CST
Matt and I talked about:
- The state of image access libraries
- The state of current forensic tools
- The Mantarayforensics project Virusshare hash sets (https://sourceforge.net/projects/mantarayforensics/files/VirusShare_Hash_Sets/)
- Achoir (https://github.com/omenscan/achoir)
- USB Detective (https://usbdetective.com/)
- Magnet Forensics User Summit (https://www.magnetusersummit.com/)
- Our next CTF at the magnet forensics user summit
I'm behind on podcast uploads again, I'll get that fixed.
You can watch the video here:
Also Read: Daily Blog #552 (A)















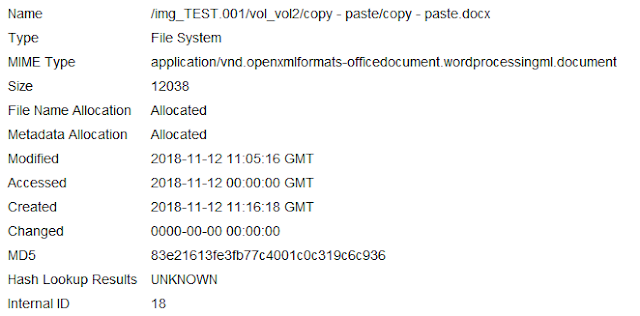
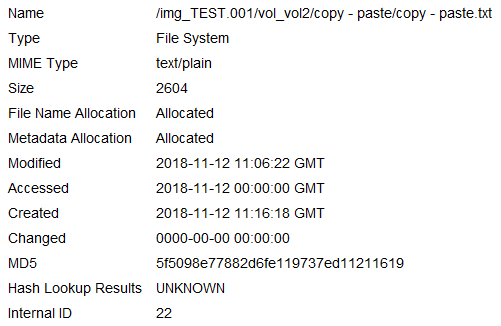
.png)
.png)
.png)
.png)




