Hello Reader,
So my plan was to do a test kitchen and show to search the CloudTrail logs for evidence that the EBS Block API was used. I thought this was important as attackers could be extracting sensitive data out of a snapshot without showing any signs of large transfer.
Well as it turns out ... it's not logged?
To test this I first went into the CloudTrail service in AWS and looked for the events in days prior that would show me creating snapshots, listing blocks and extracting blocks from snapshots.
I assigned an IAM role to the EC2 Instance that allowed me to track all of the actions associated with the instance to the API. I filtered for the user name that was generated by IAM for the role and found well ... nothing related to what I did other than creating the snapshot.
I was quite confused, so I decided to just test it again. First I just extracted blocks again and waited the 10+ minutes for the CloudTrail logs to show up.. still nothing
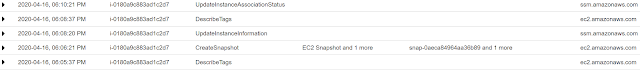
Next I thought well maybe I'm just not seeing the event because its being named something I'm not expecting. So I created a new snapshot knowing that it would show up in the logs and be an anchor for the events that came next. After creating the new snapshot I listed all the blocks and then extracted one.
Here is what I got in the logs:
So my plan was to do a test kitchen and show to search the CloudTrail logs for evidence that the EBS Block API was used. I thought this was important as attackers could be extracting sensitive data out of a snapshot without showing any signs of large transfer.
Well as it turns out ... it's not logged?
To test this I first went into the CloudTrail service in AWS and looked for the events in days prior that would show me creating snapshots, listing blocks and extracting blocks from snapshots.
I assigned an IAM role to the EC2 Instance that allowed me to track all of the actions associated with the instance to the API. I filtered for the user name that was generated by IAM for the role and found well ... nothing related to what I did other than creating the snapshot.
I was quite confused, so I decided to just test it again. First I just extracted blocks again and waited the 10+ minutes for the CloudTrail logs to show up.. still nothing
Next I thought well maybe I'm just not seeing the event because its being named something I'm not expecting. So I created a new snapshot knowing that it would show up in the logs and be an anchor for the events that came next. After creating the new snapshot I listed all the blocks and then extracted one.
Here is what I got in the logs:
You can see the snapshot being created but I don't see any indication that any block access has occurred, even though this is an API call it doesn't seem to be logged.
I checked the CloudTrail logs in the other region I've been using and again nothing there.
So from my current testing I can say that CloudTrail has gaps in its visibility, maybe this is because its a new API or maybe there are other dark corners we need to explore. So expect this to continue. We will be experimenting with AWS and determining what can be gleaned from it.
Also Read: Daily Blog #674







Post a Comment