Hello Reader,
This week was really tough as I got a lot of really good submissions. In the end the winning submission from Phil Moore was selected because much like the other submissions that made it to the final round of consideration he listed which apps he tested that contained Zone.Identifiers and what different data points they contained. But Phil took it one step further and not only tested the application he tested the behavior such as saving different file types in IE or different moods of operation like InPrivate Browsing. Last Phil added in a bonus OSX artifact to boot.
Here was the challenge:
The Challenge:
Zone.Identifier alternate data streams have been around for awhile please answer the following questions.
1. What version of Windows introduced zone.identifier
2. What data is contained with in a zone.identifier
3. What sets the zone.identifier
4. what conditions causes them to be created
5. What are the limitations of zone.identifier
So here is this week's winning entry from Phil Moore.
1. What
version of Windows introduced zone.identifier
Windows Xp sp2
Reference:
2. What
data is contained with in a zone.identifier
This relates to data stored in the registry in
the Zones key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\Zones
Until recently, the only information located within the ZoneID Alternate Data Stream related to the above settings:
Jaco Swanepoel eventually did figure out how
to do it. I haven’t been able to replicate the HostIpAddress yet.
What this means is that we can also find the
location from which the file originated in some instances, and also infer the
browser used to download the file.
3. What
sets the zone.identifier
As above, the browser checks the registry
(NTUSER.DAT) and acts accordingly.
The domains that have been stored can be
located here:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains and EscDomains.
Adding items to these keys can be done through
Internet Options:
The Internet Options can be accessed through
Windows Settings or Internet Explorer.
As a test, I added a site to the restricted
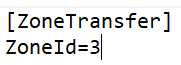
list and when saving the item, I observed that it had a ZoneID of 4.
Similarly,
if I added an item to “Trusted” then it doesn’t get a ZoneID
4. What
conditions causes them to be created
“Browsers and other internet clients (e.g.
email and chat programs) can participate in the MOTW-marking system by using
the IAttachmentExecute interface’s methods or by writing the Alternate Data
Stream directly.” (Reference: https://textslashplain.com/tag/security/page/2/)
Forensic Wiki indicates that ZoneID’s were
originally set when a file was downloaded using “Internet Explorer, Outlook,
and Windows Messenger”.
I performed a majority of my testing on Win10;
there’s plenty more to do however.
|
Task
|
ZoneID?
|
ADS Contents
|
|
Save picture (IE)
|
No
|
|
|
Save ZIP (IE)
|
Yes
|
ZoneID
|
|
Save file (Chrome, Chrome-based browser)
|
Yes
|
ZoneID
RefererURL
HostURL
|
|
Save file (Firefox)
|
Yes
|
ZoneID
|
|
Save file (Edge)
|
Yes
|
ZoneID
LastWriterPackageFamilyName (Application name)
|
|
File saved out of Outlook (o365 desktop)*
|
Yes
|
ZoneID
|
|
File saved out of Mail “Trusted Microsoft
Store” app*
|
Yes
|
ZoneID
|
|
File saved out of Skype “Trusted Microsoft
Store” app
|
Yes
|
ZoneID
|
|
Skype (Classic) App
|
Yes
|
ZoneID
|
|
Wget under Windows Subsystem for Linux
|
No
|
|
|
Powershell
|
No
|
|
|
FTP.exe (inbuilt)
|
No
|
|
|
Tor Browser Bundle (Firefox)
|
Yes
|
ZoneID
|
|
Private Browsing (IE - Zip)
|
Yes
|
ZoneID
|
|
Private Browsing (Firefox - Zip)
|
Yes
|
ZoneID
|
|
Private Browsing (Chrome - Zip)
|
Yes
|
ZoneID
RefererURL
HostURL
|
|
Private Browsing (IE - Zip
|
Untested - download kept failing
|
|
|
Save a webpage to the desktop from a link
(Chrome)
|
Yes
|
ZoneID
RefererURL
HostURL
|
|
Save current page***
|
No
|
|
|
Telegram (Windows)
|
No
|
|
|
Sync with Mega
|
No
|
|
|
Sync with Dropbox
|
No**
|
|
|
Sync with OneDrive
|
No
|
|
*apparently you can also drag and drop files
from emails and these won't be given the zoneID however this wasn’t tested.
** Dropbox does create ADS’s for the files,
but not a ZoneID.
*** Indication of originating URL identified
in the saved HTML code.
On Windows 7 I observed ZoneIDs from saving
files out of webpages, however no additional data was located.
I did not have a Windows 8/8.1 sytsem to test.
Internet Explorer doesn’t always create
ZoneIDs, for example saving a picture did not create a ZoneID. All other
browsers did however for the same test. As a guess, any file that IE thinks the
user needs to be protected from should have a ZoneID.
5. What
are the limitations of zone.identifier
Didier Stevens wrote a a post about
propagation of ZoneIDs from ISO containers.
For example, if you open an ISO in Win10 and
open the file, the file will not identify that it has come from the Internet
(and I would guess if you copied it out it would not transfer the ZoneID with
it).
Addendum:
MacOS
NTFS Drives
If you save a file to an NTFS drive using the
Tuxera NTFS driver for MacOS you don’t get a ZoneID, but you do get Extended
Attributes.
Program
Execution:
On win8 if a program is executed and smart
screen is displayed, if the user bypasses smartscreen to execute the
application then this will replace the ZoneID with “AppZoneId=4”. This is not
to be confused with “ZoneID=4” which would mean that the file came from a
restricted zone.
I do not have a Win8 system to test this on, and was unable to replicate it on
Win10.
This is another execution artefact however.
Removing
ZoneIDs:
If you download an executable from the web you will get a Security Warning. If
you deselect the “Always ask before opening this file” then the ZoneID will be
removed.
Alternatively, if you go to the properties of
the executable and select “Unblock” it will also remove the ZoneID.