Hello Reader,
Last week we talked about how to build WinFE to put on our Multiboot Thumbdrive. Now let's show a step by step guide to building WinFE light in case you are tight on space or on a system with very little resources.
This is a visual guide to compliment Colin Ramsden’s
guidance on building Windows FE
Lite. This is another great,
light-weight tool to have around, especially if you’re not comfortable with the
Linux environment when booting a device for imaging.
Get the
Prerequisites:
11.
Windows 7 computer with 20 GB or more free
space.
a.
Disable User Account Control (optional)
b.
32-bit is recommended for supporting older
architecture. 64-bit can be used, just
be consistent during the build. These
instructions and links will be for 32-bit.
c.
I installed a fresh, new copy of Windows 7
Ultimate SP 1 for this demonstration.
44.
Windows 7 x86 ISO or Disc
a.
Ultimate or Enterprise
55.
Windows XP Professional SP3 x86 ISO or Disc
(Optional)
88.
Programmers Notepad -- http://pnotepad.googlecode.com/files/pn2342350_multilang.exe
a.
Optional, though as Colin notes, you can edit
the build to suit your needs.
99.
HFS+ Drivers --
support.apple.com/downloads/DL1443/en_US/BootCamp_3.3.exe
a.
Optional.
However this is can add support for HFS+ volumes.
b.
Might as well include them. Leaving them out requires editing the batch
file. Aside from not having HFS+
support.
Now we Begin:
11.
Install WAIK from the ISO or burned Disc, to the
default directory:
This is the KB3AIK_EN
(WAIK install file) mounted via Virtual CloneDrive.
Simply select Windows AIK Setup to begin installation.
22.
Install Explorer++ and 7-Zip.
33. Extract files from
Windows 7 and XP (Optional) install Discs or ISO
a.
To keep things organized, create four folders to
sort the files you will need. Per
Colin’s example, create a “Repository” folder, then within this folder create
“Drivers”, “Windows7Files”, “WindowsXPFiles”
b. Use 7-zip to access
the Windows 7 Installation ISO or to access the Disc for Windows 7.
c.
Navigate to “Sources”
d. Then find
“install.wim” within the directory.
e. Double clicking
“install.wim” inside 7-Zip will open the file to reveal its contents.
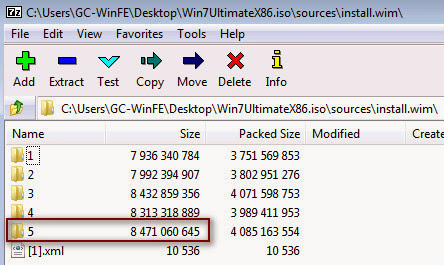
f.
Export out the largest folder that appears, to
the Window7Files folder created in step 3a.
In this case, folder 5.
g.
Optional – Use 7-Zip to access the Windows XP
installation ISO or Disc. Go into the
I386 folder and export files, to the WindowsXPFiles folder, that can add some extra
features. Colin suggests the following
list, just double click to find the executable.
i.
CALC.EX_ (calc.exe)
ii.
MAG_HOOK.DL_ (mag_hook.dll)
iii.
MAGNIFY.EX_ (magnify.exe)
iv.
MSPAINT.EX_ (mspaint.exe)
v.
MSSWCH.DL_ (msswch.dll)
vi.
MSTSC.EX_ (mstsc.exe)
vii.
MSTSCAX.DL_ (mstscax.dll)
viii.
OSK.EX_ (osk.exe)
h. Optional – Use 7-Zip
to extract drivers for HFS+ support by navigating to the “BootCamp_3.3.exe”
file downloaded from step 9 of the prerequisites. Right-click on the file and select “Open
Inside”. Now double-click entries in
this order:
i.
.rsrc
ii.
0
iii.
MSP_RESOURCE
iv. UPDATE32
v.
PCW_CAB_BootCamp
There are two files here to
extract. “AppleHFS.sys” and
“AppleMNT.sys” Place these in the “Drivers” created in Step 3a.
44.
Extract the WinFE full package from step 10 in
the prerequisites to the location of your choice. I choose simply under the C: drive. Do not alter the names of the files and
directories extracted from the package, as they are needed for the batch script
we will be using.
Let’s Build it:
Here is a little information about the folders from the
extracted FE_Lite directory.
ISO – This is where our built ISO will be output.
X – User files can be added to this folder and sub-directories
Other folders – used in the build process
Where to copy files:
\X\Windows\System32
ExplorerFrame.dll (From \Repository\Windows7Files\5\Windows\System32)
calc.exe
(From \Repository\WindowsXPFiles)
mag_hook.dll (From
\Repository\WindowsXPFiles)
magnify.exe (From
\Repository\WindowsXPFiles)
mspaint.exe (From
\Repository\WindowsXPFiles)
msswch.dll (From
\Repository\WindowsXPFiles)
mstsc.exe (From
\Repository\WindowsXPFiles)
mstscax.dll (From
\Repository\WindowsXPFiles)
osk.exe (From
\Repository\WindowsXPFiles)
Explorer.exe (Renamed
from Explorer++ which was downloaded earlier)
This is how the “\X\Windows\System32” directory should look
now (assuming you show extensions, of course).
Updates to WProtect.exe (used for Write Protection and mounting) can be
added to this folder prior to a rebuild.
Also you can adjust the wallpaper for the build by including a BMP file
of choice named “winpe.bmp”
\X\Windows\System32\Drivers
AppleHFS.sys
AppleMNT.sys
Press the button!
Open a command prompt and run the MakeFELite.bat file. There will be a lot of information scrolling
on the screen as it goes through the batch file. Then it will be done.
You can copy the
resulting image to a CD or thumbdrive, or just load it into a VM to check it
out. But this will give you a command
prompt to play around in. Add other
tools and rebuild to you hearts desire.