Hello Reader,
I thought it would be helpful for many of you who want to get some practice to walk through how to solve the image we used for last weeks Sunday Funday. This image is actually based on chapter 13 of the new book 'Infosec pro guide to computer forensics' but you don't need to buy it to learn how to do forensics.
I thought it would be helpful for many of you who want to get some practice to walk through how to solve the image we used for last weeks Sunday Funday. This image is actually based on chapter 13 of the new book 'Infosec pro guide to computer forensics' but you don't need to buy it to learn how to do forensics.
In this post I'm going to start with how to map out with USB devices were connected to the system. I am going to do this the easier way by exporting the right artifacts and then loading it into Woanware's USB Device Forensics after exporting them from the vhd image with FTK Imager.
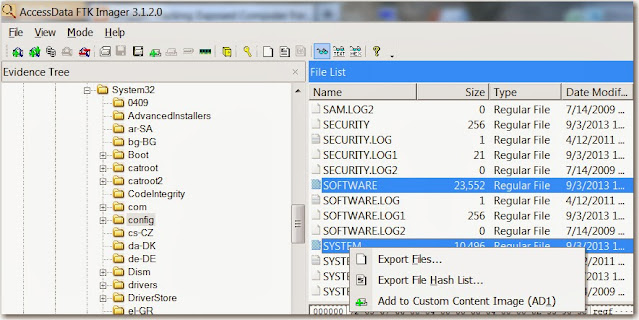
First export the System and Software registry keys found under \windows\system32\config
First export the System and Software registry keys found under \windows\system32\config
Next export the setupapi.dev.log from the \windows\inf directory as this is a windows 7 system in order to get the most accurate first plugin time.
There you go that is my easy go to way of getting external devices into an easily reviewable and with some good color coding an easy deliverable to those who are requesting the information.
Tomorrow is another forensic lunch and then we will continue to show to examine this image next week!












Post a Comment