Hello Reader,
I've been wondering in the last several posts about what happens to exported messages when different users edit the message. I finally got a chance to test this today and document my results here. To do this I exported a message from my SANS FOR500 instructor laptop on to a USB external storage device.
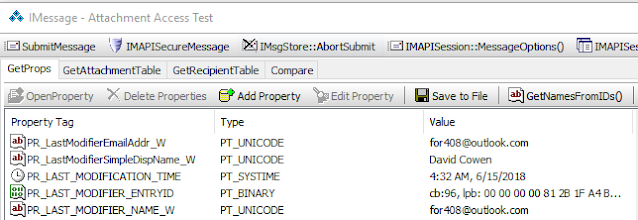
Once I exported the message I loaded up the message on my SANS instructor laptop and with Outlook spy inspected the last modification time and name.
Next I took that external storage device and I plugged it into my surface book where I usually write these blog posts and opened up the message from the external storage drive to see if just opening it as another user would change this data.
As you can see nothing changed which is what I was hoping would be true.
However what happened next surprised me. In order to try to modify the message and get the Extended MAPI fields to update with my work email address of dcowen@g-cpartners.com I did the following:
1. I set a follow up flag as completed
2. I replied to the message
3. I removed a file attachment from the message
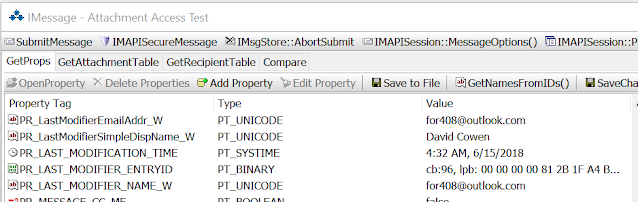
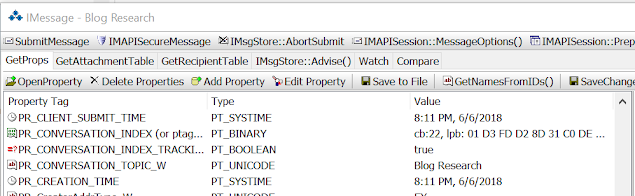
After I did each step I checked the Extended MAPI and found that the values didn't change! This is what the Extended MAPI fields looked like after I did all three things.
Notice that PR_LAST_MODIFIER_NAME_W and PR_LAST_MODIFICATION_TIME have not changed from the prior screenshot. However notice that PR_LAST_VERB_EXECUTED was set to a reply value (102) and that the PR_LAST_VERB_EXECUTION_TIME had been updated to reflect when i replied to the message on my surface book.
Now I was doing these against the exported message directly without bringing it back into Outlook. Next week I will attempt to import a message into Outlook from an exported message from another mailbox and see if this behavior changes.
I've been wondering in the last several posts about what happens to exported messages when different users edit the message. I finally got a chance to test this today and document my results here. To do this I exported a message from my SANS FOR500 instructor laptop on to a USB external storage device.
Once I exported the message I loaded up the message on my SANS instructor laptop and with Outlook spy inspected the last modification time and name.
Next I took that external storage device and I plugged it into my surface book where I usually write these blog posts and opened up the message from the external storage drive to see if just opening it as another user would change this data.
As you can see nothing changed which is what I was hoping would be true.
However what happened next surprised me. In order to try to modify the message and get the Extended MAPI fields to update with my work email address of dcowen@g-cpartners.com I did the following:
1. I set a follow up flag as completed
2. I replied to the message
3. I removed a file attachment from the message
After I did each step I checked the Extended MAPI and found that the values didn't change! This is what the Extended MAPI fields looked like after I did all three things.
Notice that PR_LAST_MODIFIER_NAME_W and PR_LAST_MODIFICATION_TIME have not changed from the prior screenshot. However notice that PR_LAST_VERB_EXECUTED was set to a reply value (102) and that the PR_LAST_VERB_EXECUTION_TIME had been updated to reflect when i replied to the message on my surface book.
Now I was doing these against the exported message directly without bringing it back into Outlook. Next week I will attempt to import a message into Outlook from an exported message from another mailbox and see if this behavior changes.
Continue Reading: Daily Blog #392 - Exploring Extended MAPI Part 6