Hello Reader,
Everything changes and we can never rest when it comes to testing and validating our forensic artifacts. This time the change has come to large external storage drives, such as the Seagate USB 3.0 drive I have next to me. If you've been doing USB forensics lately you may have noticed a conspicuous lack of large external storage drives lately in your tool reports. This is because the underlying driver has changed away from USBStor and SAS to Storport.
You read Microsoft's write-up on Storport here: https://docs.microsoft.com/en-us/windows-hardware/drivers/storage/storport-driver
First notice that the drive I have attached a Seagate Backup Plus drive with Serial Number NA9G5MN0 does not appear in the USBStor Key:
Everything changes and we can never rest when it comes to testing and validating our forensic artifacts. This time the change has come to large external storage drives, such as the Seagate USB 3.0 drive I have next to me. If you've been doing USB forensics lately you may have noticed a conspicuous lack of large external storage drives lately in your tool reports. This is because the underlying driver has changed away from USBStor and SAS to Storport.
You read Microsoft's write-up on Storport here: https://docs.microsoft.com/en-us/windows-hardware/drivers/storage/storport-driver
First notice that the drive I have attached a Seagate Backup Plus drive with Serial Number NA9G5MN0 does not appear in the USBStor Key:
Storport allows for faster drive access than the previous driver could provide which is why the slower flash drives are still using and creating USBStor artifacts while newer faster drives are loading Storport drivers.
This is important as which registry keys we can rely on to find these devices has changed.
To start with we can look at the DeviceClasses GUID
{2accfe60-c130-11d2-b082-00a0c91efb8b}
https://docs.microsoft.com/en-us/windows-hardware/drivers/install/guid-devinterface-storageport
This GUID is the Storport devices GUID and in the below screenshot we can see my internal nvme drive is located here, a VHD I mounted previously and lastly the external storage drive I plugged in.
Notice that the serial number recorded is listed as "MSFT30NA9G5MN0"
Microsoft for Storport devices appears to be prepending the MSFT30 to the serial numbers and then the actual drive serial number follows, NA9G5MN0 which I can verify is the serial number printed on the drive.
In addition the DeviceClass GUID
{a5dcbf10-6530-11d2-901f-00c04fb951ed}
https://docs.microsoft.com/en-us/windows-hardware/drivers/install/guid-devinterface-usb-device
Which is for all USB devices regardless of driver loaded you can see my attached drive below:
Next comes the key from the Windows Portable Devices Key which will reveal the volume name of the drive:
And the USB key which will show the basic USB info
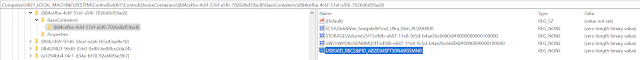
Which lead me to the question, where there some key I wasn't aware of that would allow me to connect all of these elements to understand that the volume label found in the Windows Portal Devices Key corresponded to the serial number recorded in the others. This is when I found a key I wasn't previously paying attention to called DeviceContainers.
Looking closer
we can see that this key connects the SCSI device description for the Storport driver loaded with the 0'd out serial number to the Volume GUID in the Storage and Windows Portal Devices key to the USB enum key which reveals the VID, PID and actual serial number of the drive.
Now I just need to put this into code which I'll likely do this week in the Test Kitchen as every case that involves USB storage analysis will need this logical added now.
Also Read: Daily Blog #535











Post a Comment