Hello Reader,
This week Lodrina Cherne swooped in with some interesting research that went way beyond URL history. I think what Lodrina has submitted here is the base of some very interesting research that needs to be performed to find out more. I am happy to say I received more submissions this week but I would encourage anyone reading this to give these challenges a try and submit an answer. You can only benefit from the research and possibly the win!
The Challenge:
This week Lodrina Cherne swooped in with some interesting research that went way beyond URL history. I think what Lodrina has submitted here is the base of some very interesting research that needs to be performed to find out more. I am happy to say I received more submissions this week but I would encourage anyone reading this to give these challenges a try and submit an answer. You can only benefit from the research and possibly the win!
The Challenge:
For Edge, Chrome and Firefox where could you find
evidence of what was uploaded to a file sharing site.
Please
include all of the locations available, not just the url history
The Winning Answer:
Lodrina Cherne @hexplates
Here are some general methods to investigate upload activity
in browsers:
RESEARCH! Besides
searching your favorite forensic blogs, browsers and web applications may have
developer documentation online.
In the past I’ve used Yahoo! Mail developer docs to better
understand webmail artifacts. APIs and handles are sometimes documented for
third party developers, use this to your advantage!
This snippet is as example specifically related to
advertiser data upload – so if I was interested in in this artifact, one search
term might be
“status”:
“completed”
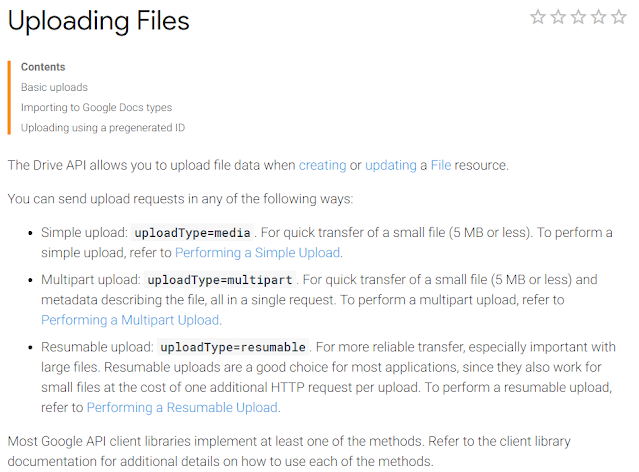
Here’s an example related to Google Drive
upload:
My search term for Google Drive uploads might be
uploadTime=
Mozilla (FireFox) has a good collection of APIs, here are
some upload related ones we might see:
What the MDN web docs tell us is that bytes and file path +
name are properties used in “UploadData”. There’s also browser compatibility
information – so this may apply with Chrome or FireFox on Android? Pretty cool!
These events may leave some of the above keywords on disk –
but even more important than the keywords, we know that there is some kind of marker that the upload has started, that it’s
completed successfully, etc. We know this data is being recorded somewhere,
even temporarily, so it’s worth digging for this type of data on disk!
TEST! For
different web applications, what is the expected behavior? Are there keywords
that appear on screen or a string in the site URL?
Here’s one example using the Dropbox browser interface with
Chrome. I am dragging and dropping a file from my system into Dropbox. Note the
on screen prompt “upload to the folder”.
While the file is uploading, we see “Uploading Additional
Forensic Resources.docx” at the bottom of the screen.
When the upload is complete, the status changes to “Uploaded
Additional Forensic Resources.docx”
upload
to the folder
Uploading
[filename of interest]
Uploaded
[filename of interest]
These search terms could be run in your forensic tool across
browser artifacts like history and cache. Using a forensic suite for your first
pass search can be useful to look across different locations and filetypes. Are
you searching inside SQLite databases? Decompressing FireFox session history?
Not every suite will do this for you though they will be more efficient than
searching each database or cache folder by itself on your first pass!
Besides browser artifacts, you could run these keywords
across other areas of the drive like unallocated space and the
pagefile/hibernation file.
Another test could be uploading a file with a unique name to
a filesharing site, then search your browser data for that filename.
Also Read: Daily Blog #455













Post a Comment