Well hello there reader,
I admit I was watching the barefoot contessa's 'back to basics' show before i wrote this so the title is most likely influenced by delicious food.
I think a lot of people have forgotten about DVDs and CDs as important forensic evidence with the widespread use of cheap reusable USB storage (commercially introduced in December 2000 (Thanks wikipedia!)), but back when I got started (1999) it was very much 'a thing'. There are four important things we can determine forensically from a CD/DVD.
1. The volume name of the CD (always)
2. When it was burned (always)
3. What software made the CD (sometimes)
4. The previous burns (always)
and some easter eggs.
1. The volume name of the CD
I think a lot of people have forgotten about DVDs and CDs as important forensic evidence with the widespread use of cheap reusable USB storage (commercially introduced in December 2000 (Thanks wikipedia!)), but back when I got started (1999) it was very much 'a thing'. There are four important things we can determine forensically from a CD/DVD.
1. The volume name of the CD (always)
2. When it was burned (always)
3. What software made the CD (sometimes)
4. The previous burns (always)
and some easter eggs.
1. The volume name of the CD
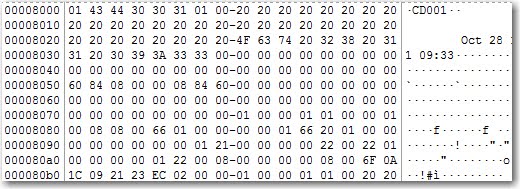
All of the CDs I reviewed start with a ISO9660 session on the disk which began at an offset of 8000. You can see in the screenshot below that standard identifier has been set as 'CD001' which is the default for most burners when a ISO9660 session is selected. However what we care about is right after that the name of the CD is ' Oct 28 11 09:33'.
You may think, why do I care about this, this is the volume name that I can see in any tool? Well if you have a multi session disk the volume name will be set to the current session, this may be the only way you have to determine the labels of the prior sessions. We will talk more about sessions in 4.
2. When it was burned
Near the end of the ISO9660 session block are four time stamps, I've always seen them set to the same time. This is the time the CD/DVD was created.
Let's break the timestamp down to a more readable form:
2011102808333500è
2011102808333500è
2011102808333500è
2011102808333500è
As you can see each of them terminates with ascii character è which is hex E8. Breaking down an individual entry we can see that the time is:
2011 10 28 08 33 3500
So October 28, 2011 at 8:33:35am is when the CD was burned, notice this is one hour off of the CD label time. Note that this time is only as accurate as the system clock that burned the CD/DVD.
3. What burned it
Depending on what software burned the CD/DVD many of them will also place the name and version of the software in the reserved space of the ISO9660 session start. In our example we can see that the name of the software that burned it is 'PRASSI2.1.374'.
Doing some quick searches for 'Prassi cd burning software' reveals that this is Primo Prassi version 2.1.374 a now defunct company whose software was bundled with some CD/DVD burners.
Why do we care? If you are trying to prove that a CD/DVD was burned on a particular system matching the software name and version to what was installed on the system can be one indicator that you can use.
4. The previous burns
If you are inspecting a rewritable CD/DVD and it has had more than one write burned to it, then each of the writes are still available. There are multiple layers of burnable media within a rewritable disk and when inserted into a CD/DVD ROM your computer will only show the most recent session. When you image the CD/DVD using a tool like FTK Imager all the prior sessions will be viewable. This is why determining the name of the session may be important as we detailed in 1.
5. Easter Eggs
Sometimes you'll find something unexpected. The ISO9660 specification does not state what can't exist within the reserved space of the session start and systems don't parse for unused areas. For instance within MSDN DVDs you'll be Microsoft's name, address and phone number. What is contained within the session start beyond what we've described here will also depend on what the burning software programmer decided to place within it.
That's it, I hope this shined some light on a possibly forgotten set of facts. Let me know what you think, your comments help to motivate me to keep posting in between baby bottles.









Very interesting article! Reminds me of the stuff I used to do way back in the day!
ReplyDeleteWow, great article, I really appreciate your thought process and having it explained properly, thank you!
ReplyDeleteUv Ink
Really i impressed. What a wonderful presentation.Now i am happy.Thank You
ReplyDeleteSocialkik
Hmmmm.... I would have guessed all of that, but more importantly to forensics, why would it not include the OS that was used including possibly the serial number of the OS? Or what about any other serial numbers of other hardware/software that could be tracked to a suspect, if they had registered it? Most of that info seems circumstantial at best. Wait.....maybe they burned the volume label with their name and address? :-)
ReplyDeleteSorry its only what the software/iso format chooses to place there.
ReplyDeleteI like reading articles like this since this is almost an art form that is disappearing with all the push-button "Nintendo" forensic tools around. You also have a great gift to explain complex concepts in a simple manner. Feed us more, we are hungry :-)
ReplyDeleteHi David, is there a way to identify the actual time of burning if the system clock of the computer was tampered with or modified? Wouldn't the CD have its own internal clock in its system? I'm not sure if ISO 9660 has its own date and time internalized once a cd is manufactured...
ReplyDeleteHi Anonymous, sorry for the late reply.
ReplyDeleteThe CD does not have its own internal clock. The only thing you can hope for is that the event logs show the time change or that MFT records a file id out of sequence for the create time to detect that fact.
Since the time stamp in burned CDs also includes the GMT timezone offset, it should be possible to identify if a suspect modified the timezone settings before/after burning a CD. It might be possible to see time zone change patterns by comparing a few burned CDs from the suspect's collection. I have not seen other standards than ISO 9660 that includes the timezone info in its time stamps. It is also interesting to note that many of the values saved in ISO 9660 are stored in little-endian and big-endian formats most likely to be able to read it in Intel and PowerPC based hardware.
ReplyDeleteTime stamp structure:
1: Number of years since 1900
2: Month of the year from 1 to 12
3: Day of the Month from 1 to 31
4: Hour of the day from 0 to 23
5: Minute of the hour from 0 to 59
6: second of the minute from 0 to 59
7: Offset from Greenwich Mean Time in
number of 15 minute intervals from
-48(West) to +52(East)
i.e: 70070F062B1900
Meaning: 2012 May, 15 at 6:43:25 a.m. GMT-00